Warnings When Connecting to Your PC
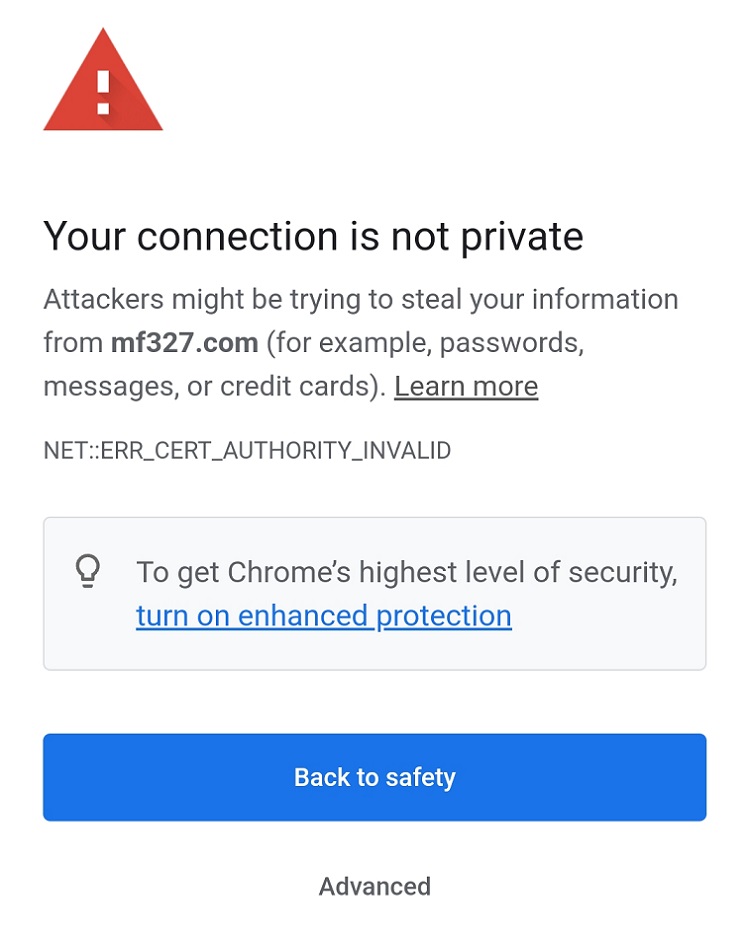
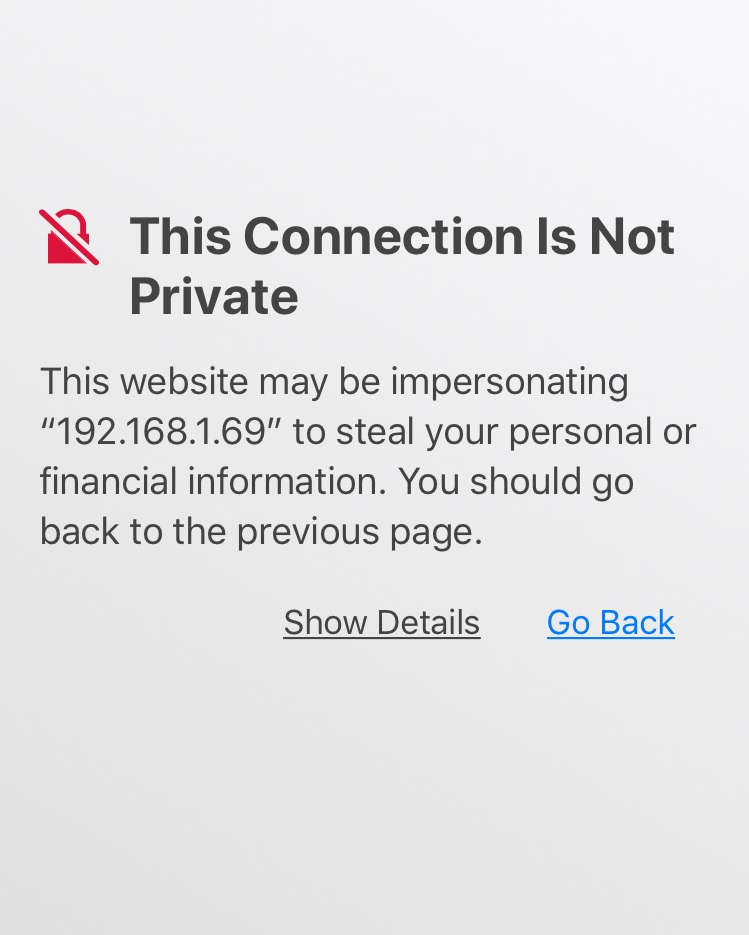
Why Am I Seeing These Warnings?
When you visit a public website, your browser looks at the site's certificate and
checks if it's signed by one of a hundred or so third-party "Certificate Authorities" (CA)
that the browser "trusts". If it is, you get a green padlock and your connection is
considered secure (assuming there are no problems with the certificate).
This type of certificate signing only works for websites with a registered domain name
(www.website.com) and static IP address (IP address that never changes), Private computers
don't typically have these things because they cost more than most people are willing to pay
for remote access to a single PC. That's where Self-Signed Certificates come in.
Self-signed certificates are certificates that you create yourself using software. When
you visit a website that uses a self-signed certificate, your browser has no way to
verify it, so it will give you a warning that says your connection is not secure.
MF327 uses Self-signed certificates.
Should I Be Concerned?
No. These warnings are intended for users accessing public websites, not a
private computer. Because you have access to the computer using the certificate,
you can verify it yourself and prove your connection is secure.
(See mf327.com/help/verify-certificate)
If you see this warning when connecting to any other website, such as your email,
online banking, or an e-commerce site, you should leave immediately.
How Do I Know My Connection Is Secure?
Because you're connecting to your own PC, you have access to the actual
certificate used by the server and can personally verify that it matches
the one shown in your browser.
Comparing certificates is easy thanks to Fingerprints. A fingerprint is a shortened
version (or hash) of a certificate used to quickly compare it against another for an exact match.
All major web browsers and operating systems have a certificate viewer that will show you a
certificate's fingerprint. Click here to see how.
How Secure Is It?
One could argue that self-signed certificates, when properly verified, are even
more secure than the ones used for online banking. Website owners typically
pay hundreds of dollars per year to have a Certificate Authority sign their
certificate so that web browsers will trust them. You can probably see a few
problems with this scenario.
- There's money involved (Money = Influence)
- There's trust involved (Trust = Vulnerability)
-
By signing certificates for thousands of high-profile websites,
Certificate Authorities make themselves a high-value target for hackers
Comparing fingerprints for a self-signed certificate is a direct verification
that costs nothing and doesn't rely on trust. You can't do this with a public
website (and neither can your browser) since you don't have access to the server.
Warnings When Installing Your Certificate
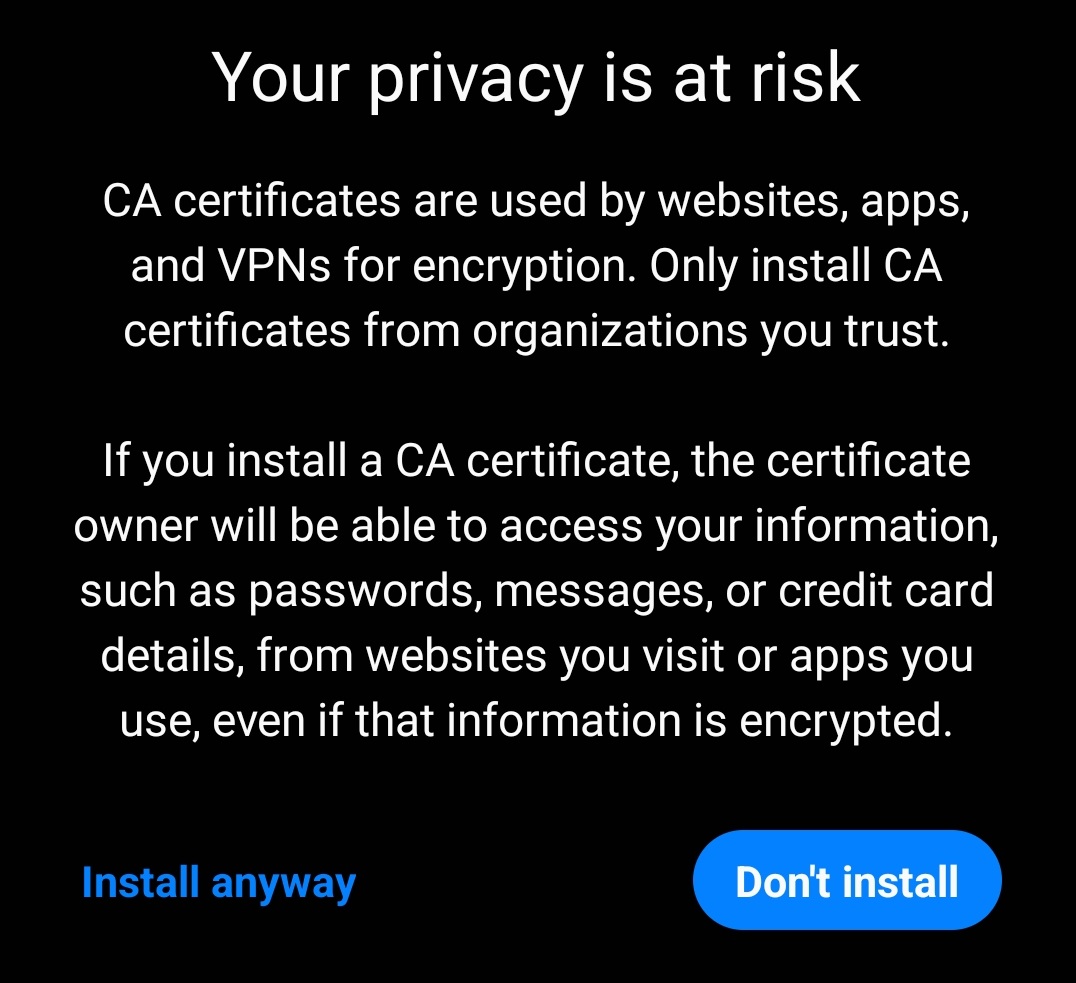
What Is a Certificate?
Certificates are used by web browsers and apps to verify that a website or
server is who it claims to be. It confirms that the server you're connected
to is the same one you typed in the address bar.
What Is a CA Certificate?
A Certificate Authority (CA) is someone that your browser trusts to verify
certificates for it. A CA verifies a certificate by confirming that the
certificate holder owns the server and then digitally signing their certificate.
If your browser sees a certificate that's signed by a CA that it trusts, it
will consider it valid. CA certificates identify CAs that your browser trusts.
Can the Owner of a CA Certificate Spy on My Data?
Since your browsers and apps will automatically trust any certificate that's
signed by a trusted CA, the owner of the CA certificate could create fake
certificates for websites you visit and your browser would trust them. But,
in order to get any data, they would need to take additional steps to trick
your browser into connecting to the wrong server, such as installing malware
on your device, hacking the router you connect to, compromising a DNS server,
or getting you to connect to a rogue Wi-Fi network.
Should I Be Concerned?
In this case, you are the certificate owner and the key needed to forge
certificates resides on your own computer. In order to perform such an
attack, a hacker would need access to your PC and control of your device,
a DNS server, or the network your device is connected to. If your PC is a
high-value target and this is a real concern for you, see the section
below titled, "Do I Need To Install My Certificate?".
Do I Need To Install My Certificate?
No. This step is entirely optional and is only required to get rid of certificate
warnings when accessing your PC. Alternatively, you can add an exception for your
PC in the web browser and verify its certificate yourself using the fingerprint.
(See mf327.com/help/verify-certificate)